Issue
- You receive the warning message Using unencrypted connection! Please configure the webserver to use HTTPS when accessing ESET PROTECT via HTTP. This occurs after the ESET PROTECT installation
- Use an existing certificate
- Create a new certificate
Solution
Use an existing certificate
The steps below refer to certificates for Apache Tomcat, which are used to ensure secure HTTPS connections. For information about ESET PROTECT certifications, see our Online Help topic.
- Move the certificate file (for example certificate_file.pfx) to a Tomcat configuration directory (for example /etc/tomcat/).
- Open the Server.xml file located in /etc/tomcat/. The Location may vary depending on the Linux distribution.
- If there is no <Connector after <Service name="Catalina"> in Server.xml, copy the following string into the Server.xml. Use your own values for keystoreFile, keystorePass, and keystoreType:
<Connector port="8443"protocol="HTTP/1.1"SSLEnabled="true"maxThreads="150"scheme="https"secure="true"clientAuth="false"sslEnabledProtocols="TLSv1.2,TLSv1.3"ciphers="TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA256,TLS_ECDHE_RSA_WITH_AES_128_GCM_SHA256,TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA,TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA384,TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384,TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA,TLS_RSA_WITH_AES_128_CBC_SHA256,TLS_RSA_WITH_AES_128_GCM_SHA256,TLS_RSA_WITH_AES_128_CBC_SHA,TLS_RSA_WITH_AES_256_CBC_SHA256,TLS_RSA_WITH_AES_256_GCM_SHA384,TLS_RSA_WITH_AES_256_CBC_SHA"keystoreFile="/etc/tomcat/certificate_file.pfx"keystorePass="Secret_Password_123"keystoreType="PKCS12" /> - If <Connector is present after <Service name="Catalina"> in Server.xml, replace the values of parameters listed below with your values:
keystoreFile - Provide the full path to the certificate file (.pfx, .keystore, or other). If you use a non-JKS certificate (for example, a .pfx file), delete the keyAlias (it is present in Server.xml by default) and add the proper keystoreType.keystorePass - Provide certificate passphrase.keystoreType- Specify the certificate type.
- If there is no <Connector after <Service name="Catalina"> in Server.xml, copy the following string into the Server.xml. Use your own values for keystoreFile, keystorePass, and keystoreType:
- Restart the Tomcat service (
sudo systemctl tomcat restart).- If you use a
.keystorefile, use the path to the file (keystoreFile="/etc/tomcat/tomcat.keystore") and definekeyAlias(keyAlias="tomcat") instead ofkeystoreType. - If you want to disable HTTP:
<!-- <Connector port="8080" protocol="HTTP/1.1"connectionTimeout="20000"redirectPort="8443" />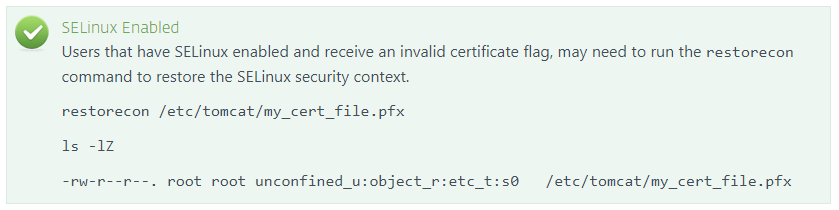
- If you use a
Create a new certificate and get it signed
Use a secure HTTPS/SSL connection  for ESET PROTECT.
for ESET PROTECT.
- Create a keystore with an SSL certificate. You must have Java installed.
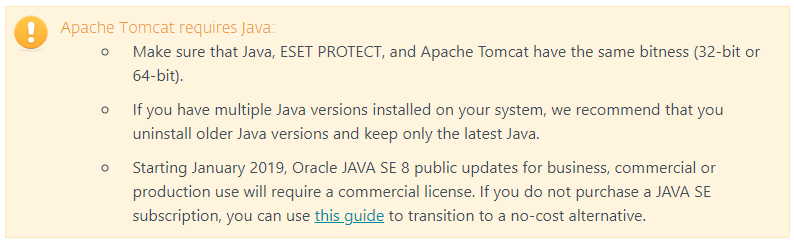
Java includes the keytool, which enables you to create a certificate via command line. You must generate a new certificate for each tomcat instance (if you have multiple tomcat instances) to ensure that if one certificate is compromised, other tomcat instances will remain secure.
Below is a sample command to create akeystorewith an SSL certificate:
Navigate to the exact location of the keytool file, for example/usr/lib/jvm/”java version”/jre/bin(the directory depends on the OS and Java version) and run the command:sudo keytool -genkeypair -alias "tomcat" -keyalg RSA -keysize 4096 -validity 3650 -keystore "/etc/tomcat/tomcat.keystore" -storepass "yourpassword" -keypass "yourpassword" -dname "CN=Unknown, OU=Unknown, O=Unknown, L=Unknown, ST=Unknown, C=Unknown"
The file path/etc/tomcat/tomcat.keystoreis only an example, choose your own secure and accessible destination.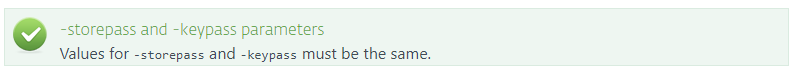
- Export the certificate from the keystore. Below is a sample command to export the certificate sign request from the keystore:
sudo keytool -certreq -alias tomcat -file "/etc/tomcat/tomcat.csr" -keystore "/etc/tomcat/tomcat.keystore" -ext san=dns:ESETPROTECT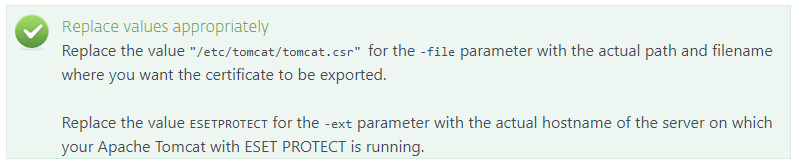
- Get the SSL certificate signed with the Root Certificate Authority (CA) of your choice.
You can proceed to step 6 if you plan to import a Root CA later. If you choose to proceed this way your web browser may display warnings about a self-signed certificate and you will need to add an exception to connect to ESET PROTECT via HTTPS.
- Import the root certificate and intermediate certificate of your CA to your
keystore. These certificates are usually made available by the entity that signed your certificate. It is necessary because the certificate reply is validated using trusted certificates from thekeystore.
sudo keytool -import -alias root -file "/etc/Tomcat/root.crt" -keystore "/etc/tomcat/tomcat.keystore"
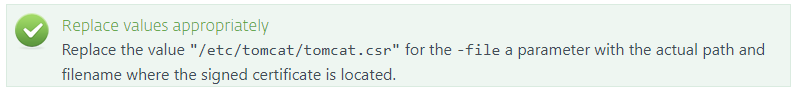
sudo keytool -import -alias intermediate -file "/etc/Tomcat/intermediate.crt.pem" -keystore "/etc/tomcat/tomcat.keystore" - When you receive the signed certificate with the Root CA, import the public key of CA and the certificate (tomcat.cer) into your keystore. Below is a sample command that imports a signed certificate into the keystore:
sudo keytool -import -alias tomcat -file "/etc/tomcat/tomcat.cer" -keystore "/etc/tomcat/tomcat.keystore"
- Edit the
server.xmlconfiguration file so that the tag<Connectoris written similar to the example below:<Connector server="OtherWebServer" port="443" protocol="org.apache.coyote.http11.Http11NioProtocol" SSLEnabled="true" maxThreads="150" scheme="https" secure="true" clientAuth="false" sslProtocol="TLS" keystoreFile="/etc/tomcat/tomcat.keystore" keystorePass="yourpassword"/>
This modification also disables non-secure Tomcat features, leaving only HTTPS enabled (scheme=parameter). For security reasons, you may also need to edittomcat-users.xmlto delete all Tomcat users and change ServerInfo.properties to hide the identity of the Tomcat. - Restart the Apache Tomcat service. ESET PROTECT may use the service name
tomcat9.sudo systemctl tomcat restart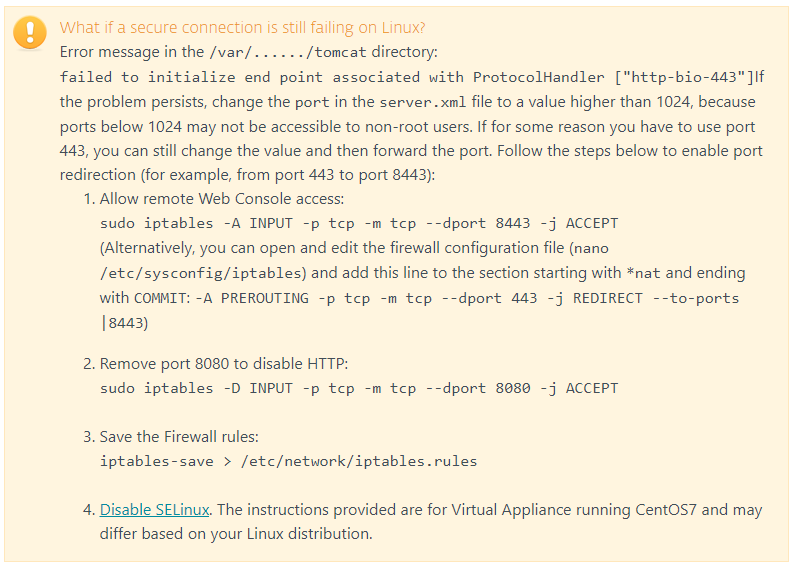
Add a comment
Please log in or register to submit a comment.